Abstract
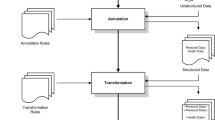
The average costs of data leakage are steadily on the rise. Especially in healthcare, the disclosure of sensitive information may have unfavorable consequences for the patient. As a consequence, several data security and access control mechanisms have been introduced, ranging from data encryption to intrusion detection or role-based access control, doing a great work in protecting sensitive information. However, the majority of these concepts are centrally controlled by administrators who are a major threat to the patients’ privacy. Apart from administrators, other internal persons, such as hospital staff members, may exploit their access rights to snoop around in private health data. This work presents PERiMETER, a security protocol for data privacy that is strictly controlled by the data owner. It integrates pseudonymization and encryption to create a methodology that uses pseudonyms as access control mechanism, protects secret cryptographic keys by a layer-based security model, and provides privacy-preserving querying.






Similar content being viewed by others
References
Abouakil D, Heurix J and Neubauer T (2011) Data models for the pseudonymization of DICOM data. In Proceedings of the 2011, 44th Hawaii International Conference on System Sciences (HICSS’11), pp 1–11, IEEE Computer Society, Washington, DC.
Bouchard S (2011) Three of top 6 data breaches of 2011 were in healthcare. Healthcare Finance News, 19 December.
Camenisch J, Shelat A, Sommer D, Fischer-Hübner S, Hansen M, Krasemann H, Lacoste G, Leenes R and Tseng J (2005) Privacy and identity management for everyone. In Proceedings of the 2005 Workshop on Digital Identity Management (DIM’ 05), pp 20–27, ACM, New York.
Carr J (2002) Strategies and issues: thwarting insider attacks. Network Magazine, September 5.
Cunningham H, Maynard D and Bontcheva K (2011) Text Processing with GATE. Gateway Press, California.
Damiani E, di Vimercati SDC, Finetti M, Paraboschi S, Samarati P and Jajodia S (2004) Implementation of a storage mechanism for untrusted dbmss. In Proceedings of the Second IEEE International Security in Storage Workshop (SISW’03), p 38, IEEE, Washington, DC.
Damiani E, di Vimercati SDC, Jajodia S, Paraboschi S and Samarati P (2003) Balancing confidentiality and efficiency in untrusted relational DBMSs. In ACM Conference on Computer and Communications Security (Jajodia S, Atluri V and Jaeger T, Eds), pp 93–102, ACM, New York.
Dolin RH, Alschuler L and Beebe C (2001) The hl7 clinical document architecture. Journal of the American Medical Informatics Association 8 (6), 552–569.
Eggers WD (2007) Government 2.0: Using Technology to Improve Education, Cut Red Tape, Reduce Gridlock, and Enhance Democracy. Rowman and Littlefield, Lanham, MD.
Ferraiolo DF and Kuhn R (1992) Role-based access controls. In 15th National Computer Security Conference, 13–16 October, pp 554–563, NIST, Baltimore, MD.
Ferraiolo DF, Sandhu R, Gavrila S, Kuhn R and Chandramouli R (2001) Proposednist standard for role-based access control. ACM Transactions on Information and System Security 4 (3), 224–274.
Grün K, Karlinger M and Schrefl M (2006) Schema-aware labelling of XML documents for efficient query and update processing in SemCrypt. International Journal of Computer Systems: Science & Engineering 21 (1), 65–82.
Hacigümüs H, Iyer B, Li C and Mehrotra S (2002) Executing SQL over encrypted data in the database-service-provider model. In Proceedings 2002 ACM SIGMOD International Conference on Management of Data (SIGMOD'02), pp 216–227, ACM Press, New York.
Heurix J, Karlinger M, Schrefl M and Neubauer T (2011) A hybrid approach integrating encryption and pseudonymization for protecting electronic health records. In Proceedings of the Eighth IASTED International Conference on Biomedical Engineering (Baumgartner C, Ed), pp 117–124, ACTA Press, Innsbruck, Austria.
Heurix J and Neubauer T (2011) Privacy-preserving storage and access of medical data through pseudonymization and encryption. In Proceedings of the 8th International Conference on Trust, Privacy & Security in Digital Business (TrustBus'11), Toulouse, France, pp 186–197, Springer-Verlag, Berlin, Heidelberg.
Horowitz BT (2011) Patients sue Sutter health over data breach involving 4.24 million people. Health Care IT News, 30 November.
IHE (2010) IHE IT infrastructure (ITI) technical framework 7.0.
Jammalamadaka RC and Mehrotra S (2006) Querying encrypted XML documents. Database Engineering and Applications Symposium, International, pp 129–136, IEEE Computer Society, Los Alamitos, CA.
Johnson ME (2009) Data hemorrhages in the health-care sector. In Financial Cryptography and Data Security (FC 09) (Roger D and Philippe G, Eds), pp 71–89, Springer-Verlag, Berlin, Heidelberg.
Kallahalla M, Riedel E, Swaminathan R, Wang Q and Fu K (2003) Plutus: scalable secure file sharing on untrusted storage. In Proceedings of the 2nd USENIX Conference on File and Storage Technologies (FASt’ 03), pp 29–42, USENIX Association, Berkeley, CA.
Keeney M, Kowalski E, Cappelli D, Moore A, Shimeall T and Rogers S (2005) Insider threat study: computer systems sabotage in critical infrastructure sectors, May 2005, National Threat Assessment Center, US Secret Service and CERT/SEI, [WWW document] http://www.cert.org/archive/pdf/insidercross051105.pdf, (accessed 13 February 2012).
Lechler T, Wetzel S and Jankowski R (2011) Identifying and evaluating the threat of transitive information leakage in healthcare systems. In Proceedings of the 44th Hawaii International Conference on System Sciences, pp 1–10, IEEE Computer Society, Washington, DC.
Lee J-G and Whang K-Y (2006) Secure query processing against encrypted XML data using query-aware decryption. Information Sciences 176 (13), 1928–1947.
Li N, Li T and Venkatasubramanian S (2007) t-closeness: privacy beyond k-anonymity and l-diversity. In IEEE 23rd International Conference on Data Engineering (ICDE2007) (Chirkova R, Dogac A, Özsu MT and Sellis TK, Eds), pp 106–115, IEEE, Istanbul, Turkey.
Luethi M and Knolmayer G (2009) Security in health information systems: an exploratory comparison of U.S. and Swiss hospitals. In Proceedings of the 42nd Hawaii International Conference on System Sciences, pp 1–10, IEEE Computer Society, Los Alamitos, CA.
Machanavajjhala A, Kifer D, Gehrke J and Venkitasubramaniam M (2007) L-diversity: privacy beyond k-anonymity. ACM Transactions on Knowledge Discovery Data 1 (1), 3.
NEMA (2008) Digital imaging and communications in medicine. Standard, National Electrical Manufacturers Association, Rosslyn, VA.
Neubauer T and Heurix J (2011) A methodology for the pseudonymization of medical data. Journal of Medical Informatics 80 (3), 190–207.
Neubauer T and Kolb M (2009) An evaluation of technologies for the pseudonymization of medical data. In Computer and Information Science 2009 (Lee R, Hu G and Miao H, Eds), Studies in Computational Intelligence, pp 47–60, Springer, Berlin/Heidelberg.
Noumeir R, Lemay A and Lina J (2007) Pseudonymization of radiology data for research purposes. Journal of Digital Imaging 20 (3), 284–295.
OASIS (2010) eXtensible access control markup language (XACML) version 3.0. Committee Specification 01.
Ponemon Institute (2011) Second annual benchmark study on patient privacy & data security. Research Report.
Riedl B, Grascher V and Neubauer T (2008) A secure e-health architecture based on the appliance of pseudonymization. Journal of Software 3 (2), 23–32.
RØstad L and Edsberg O (2006) A study of access control for healthcare systems based on audit trails from audit logs. In Proceedings of the 22nd Annual Computer Security Applications Conference, Miami Beach, pp 175–186.
Schrefl M, Dorn J and Grün K (2005) SemCrypt – ensuring privacy of electronic documents through semantic-based encrypted query processing. In Proceedings Int. Workshop on Privacy Data Management (PDM 2005). IEEE Computer Society Press, Washington, DC.
Shamir A (1979) How to share a secret. Communications of the ACM 22 (11), 612–613.
Sweeney L (2002) k-anonymity: a model for protecting privacy. International Journal on Uncertainty, Fuzziness and Knowledge-based Systems 10 (5), 557–570.
Thielscher C, Gottfried M, Umbreit S, Boegner F, Haack J and Schroeders N (2005) Patent: data processing system for patient data. Int. Patent, WO 03/034294 A2.
United States Department of Health & Human Service (2006) HIPAA administrative simplification: enforcement; final rule. Federal Register/Rules and Regulations 71 (32), 8389–8433.
Yang Y, Ng W, Lau HL and Cheng J (2006) An efficient approach to support querying secure outsourced XML information. In Advanced Information Systems Engineering, 18th International Conference (CAiSE 2006), Luxembourg, 5–9 June, Lecture Notes in Computer Science (Dubois E and Pohl K, Eds), Vol. 4001, pp 157–171, Springer, Berlin.
Acknowledgements
The research was funded by BRIDGE (#824884) and by COMET K1, FFG – Austrian Research Promotion Agency.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Heurix, J., Karlinger, M. & Neubauer, T. PERiMETER – pseudonymization and personal metadata encryption for privacy-preserving searchable documents. Health Syst 1, 46–57 (2012). https://doi.org/10.1057/hs.2012.5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1057/hs.2012.5