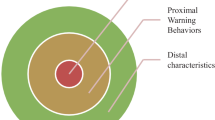
Abstract
In 2012, a team of US air marshals forced a Delta Airlines overseas flight to return and evacuate because two passengers were thought to be working as a terrorist team, which proved to be false after investigation. This incident plus two other on-plane psychological meltdowns of in-flight personnel are alarming reminders of the snap decisions that are currently made without much guidance to inform such threat assessments. Preflight security measures have addressed many of the post-9/11 threats of terrorism. Nonetheless, successful and thwarted acts of terrorism and reconnaissance response probes have fueled a growing need for homeland security, military and public safety personnel's reflexive instincts to engage, ‘what if’ as a guiding principle in threat assessments. There is an elusive nexus between timely intelligence gathering, acts of terror and understanding the mindset of a terrorist. An internalized homeland security decision-making approach to ‘think like a terrorist’ is instructive in coming up with actionable information for many contraterrorism efforts. This article raises several issues related to the mindset of a terrorist. Such mindset is reviewed from two traditional theoretical frameworks (that is, criminological and psychological theories). The article also explores the applicability of these theories to public safety from a risk assessment perspective. The article concludes with implications for public safety research, practice and training.
Similar content being viewed by others
References
Alexander, J.C. (2004) Cultural Trauma and Collective Identity. Berkeley: University of California Press.
Al-Marayati, S. (2009) Major Hasan and the Quran. Repentance is the only option for the Fort Hood killer. Wall Street Journal, 8 December, http://online.wsj.com/article/SB10001424052748704107104574571981079768944.html, accessed July 2012.
Ashish, G., Zaniewski, L. and Subramani, K. (2011) Algorithmic aspects of risk management. In: G.D. Agha (ed.) Talcott Festschrift, LNCS. Berlin, Heidelberg: Springer-Verlag, pp. 262–276.
Baum, H.S. (1987) On the Unconscious Life of Administrative Elements. The Invisible Bureaucracy: The Unconscious in Organizational Problem-Solving. New York: Oxford University Press.
Bird, G., Blomberg, S.B. and Hess, G.D. (2008) International terrorism. The World Economy (1467–9701), 31 (2): 255–274.
Boyns, D. and Ballard, J.D. (2004) Developing a sociological theory for the empirical understanding of terrorism. The American Sociologist 35 (2): 5–25.
Bugental, J.F.T. (1978) Psychotherapy and Process. New York: McGraw-Hill.
Burke, M.T. and Miller, G. (1996) Using the spiritual perspective in counseling persons with HIV/AIDS: An intergrative approach. Counseling and Values 40: 185–195.
Crenshaw, M. (2000) The psychology of terrorism: An agenda for the twenty-first century. Political Psychology 21 (2): 405–420.
Cronin, A.K. (2006) How al-Qaida ends: The decline and demise of terrorist groups. International Security 31 (1): 7–48.
Denbeaux, M. and Denbeaux, J. (2006) No-hearing hearings. CSRT: The modern habeas corpus? http://law.shu.edu/publications/guantanamoReports/final_no_hearing_hearings_report.pdf, accessed 25 March 2013.
De Borger, B., Proost, S.K. and Van Dender, K. (2008) Private port pricing and public investment in port and hinterland capacity. Journal of Transport Economics and Policy 42 (3): 527–561.
Department of Defense. (2010) Terrorism. DOD dictionary of military and associated terms, http://www.dtic.mil/doctrine/dod_dictionary/data/t/7591.html, accessed 25 March 2013.
Durkheim, E. (1933) The Division of Labor in Society, Translated by G. Simpson. New York: The Free Press.
Earnshaw, S. (2006) Existentialism: A Guide for the Perplexed, Guides for the Perplexed, 1st edn. London: Continuum International Publishing Group.
Felter, J. and Brachman, J. (2007) CTC Report: An Assessment of 516 Combatant Status Review Tribunal (CSRT) Unclassified Summaries, http://www.ctc.usma.edu/csrt/CTC-CSRT-Report-072407.pdf.
Finkelman, P. (2011) John Brown: America's first terrorist. Prologue 43 (1): 16–27.
Frankl, V.E. (2006) Man's Search for Meaning. Boston, MA: Beacon Hill Press.
Frey, R.G. and Morris, C.W. (eds.) (1991) Violence, Terrorism and Justice. New York: Cambridge University Press.
Haley, A. (1965) The Autobiography of Malcolm X, 1st hardcover edn. New York: Grove Press.
Hamilton, L.H. (2005) Fighting terrorism. Indiana Journal of Global Legal Studies 12 (2): 379–390.
Hamner, C. (2011) Booth's reason for assassination, http://teachinghistory.org/history-content/ask-a-historian/24242, accessed 12 July 2011.
Hoffman, B. (2006) Inside Terrorism. New York: Columbia University Press.
Horgan, J. (2003) The search for the terrorist personality. In: A. Silke (ed.) Terrorists, Victims and Society: Psychological Perspectives on Terrorism and Its Consequences. West Sussex, UK: John Wiley & Sons, pp. 3–27.
Johnson, R. (2011) Cultural and Ethical Issues in Delivering Services in a Forensic Psychology Setting. Paper presented at the 19th Annual Patton State Hospital Forensic Psychology Conference, San Bernardino, CA.
Johnson, R. (2012) Multinational homeland security terrorism response training for clinical and forensic psychology PTSD issues: Risk assessment heuristic. Journal of the Global Homeland Security Education Network 1 (1): 49–64.
Karp, R. and Luby, M. (1983) Monte-Carlo algorithms for enumeration and reliability problems. 24th FOCS, pp. 56–64.
Koblentz, G. (2001) Overview of federal programs to enhance state and local preparedness for terrorism with weapons of mass destruction. Executive Session on Domestic Preparedness (ESDP). Cambridge, MA: Harvard University, John F. Kennedy School of Government, http://belfercenter.ksg.harvard.edu/files/overview_of_federal_programs.pdf, accessed July 2012.
Kruglanski, A.W. and Fishman, S. (2009) Psychological factors in terrorism and counterterrorism. Social Issues and Policy Review (1751–2409) 3 (1): 1–44.
LaFree, G. and Dugan, L. (2009) Research on terrorism and countering terrorism. Crime and Justice 38 (1): 413–477.
Lepsius, O. (2004) Liberty, security and terrorism: The legal position in Germany [Electronic version]. German Law Journal 5: 435–460.
Loftus, E.F. (2011) Intelligence gathering post-9/11. American Psychologist 66 (6): 532–541.
Lum, C., Koper, C. and Telep, C.W. (2011) The evidence-based policing matrix. Journal of Experimental Criminology 7 (1): 3–26.
Mackeown, P.K. (2001) Stochastic Simulation in Physics. Secaucus, NJ: Springer-Verlag New York.
Mamdani, M. (2004) Good Muslim, Bad Muslim. New York: Doubleday.
Marino, G. (2004) Basic Writings of Existentialism. New York: Modern Library.
Maslow, A. (1998) Toward A Psychology of Being, 3rd edn. New York: Wiley.
McCauley, C. and Moskalenko, S. (2011) Friction: How Radicalization Happens to them and Us. New York: Oxford University Press.
Merari, A. and Friedland, N. (1985) Social psychological aspects of political terroriam. In: S. Oscamp (ed.) International Conflict and National Public Policy Issues: Applied Social Psychology Annual, Vol. 6. Beverly Hills, CA: Sage Publications, pp. 185–205.
Mueller, J. and Stewart, M.G. (2011) Terror, Security, and Money: Balancing the Risks, Benefits, and Costs of Homeland Security, New York and Oxford, UK: Oxford University Press.
Muhammad, N., Ahmed, M., Muhammad, M., Abdullah, O., Fazle, S. and Naqeeb, H. (2012) Honor killing in Pakistan: An Islamic perspective. Asian Social Science (1911–2017) 8 (10): 180–185.
National Counterterrorism Center 2010 Report on Terrorism. (2011) From National Counterterrorism Center, 23 March, http://www.nctc.gov/witsbanner/docs/2010_report_on_terrorism.pdf, accessed July 2012.
Nowak, M.A. and Sigmund, K. (2004) Evolutionary dynamics of biological games. Science 303 (5659): 793–799.
Osipov, V. and Ivakin, Y. (2009) Terrorists: Statistical profile. Information Fusion and Geographic Information Systems. Lecture Notes in Geo-Information and Cartography. Part 5: 241–250, doi:10.1007/978-3-642-00304-2_16.
Pantucci, R. (2011) A Typology of Lone Wolves: Preliminary Analysis of Lone Islamist Terrorists. London: International Centre for the Study of Radicalization and Political Violence (ICSR).
Pilon, M. (2012) Path of Saudi Arabian trailblazer runs through the United States. New York Times, 14 July, p. 5.
Ranstorp, M. (ed.) (2007) Mapping Terrorism Research: State of the Art, Gaps and Future Direction. Abingdon, UK: Routledge.
Rees, W. and Aldrich, R.J. (2005) Contending cultures of counterterrorism. International Affairs (1468–2346) 81 (5): 905–923.
Reynolds, D.S. (2005) John Brown, Abolitionist: The Man Who Killed Slavery, Sparked the Civil War, and Seeded Civil Right. New York: Vintage Books.
Saleh, N. (2012) London Olympics 2012: Year of the Arab woman athlete, PolicyMic. July, http://www.policymic.com/articles/11632/london-olympics-2012-year-of-the-arab-woman-athlete, accessed 25 March 2013.
Sappenfield, M. (2012) Saudi Olympic athlete hit by judo head scarf ban: Safety or discrimination? Christian Science Monitor, 27 July, p. 1.
Schmid, A. and Jongman, A. (1988) Political Terrorism: A New Guide to Actors, Authors, Concepts, Data Bases, Theories, and Literature. New Brunswick, NJ: Transaction Books.
Schulze, F. (2004) Breaking the cycle: Empirical research and post graduate studies on terrorism. In: A. Silke (ed.) Research on Terrorism: Trends, Achievements, and Failures. London: Frank Cass, pp. 161–185.
Sharf, R.S. (2010) Theories of Psychotherapy and Counseling, 3rd edn. Belmont, CA: Brooks/Cole.
Silke, A. (2003) Becoming a terrorist. In: A. Silke (ed.) Terrorists, Victims and Society: Psychological Perspectives on Terrorism and Its Consequences. West Sussex, UK: John Wiley & Sons, pp. 29–53.
Spear, J. (2003) The emergence of a European ‘strategicpersonality’ and the implications for the transatlantic relationship. Arms Control Today, 9 November, pp. 13–18.
Victoroff, J. and Kruglanski, A. (eds.) (2009) Psychology of Terrorism: Classic and Contemporary Insights. New York: Psychology Press.
Vose, D. (2000) Risk Analysis: A Quantitative Guide, 2nd edn. Hoboken, NJ: Wiley.
United States Department of Justice – Federal Bureau of Investigation. (1964) Warren Commission, Vol. XIV: CE 2121. 18 May, http://www.history-matters.com/archive/jfk/wc/wcvols/wh24/pdf/WH24_CE_2121.pdf, accessed July 2012.
Weimann, G. (2004) Cyberterrorism: How Real Is the Threat? Washington, DC: United States Institute for Peace.
Weinberg, L. and Pedahzur, A. (2010) Suicide terrorism suicide terrorism. Religion Compass 4 (4): 234–244.
Young, J.K. and Findley, M.G. (2011) Promise and pitfalls of terrorism research. International Studies Review 13 (3): 411–431.
Ziemke, C.F. (2000) The national myth and strategic personality of Iran: A counterproliferation perspective. In: V.A. Utgoff (ed.) The Coming Crisis: Nuclear Proliferation, US Interests, and World Order. Cambridge, MA: MIT Press, pp. 88–89.
Author information
Authors and Affiliations
Rights and permissions
About this article
Cite this article
Johnson, R. Forensic psychological mindset of a terrorist: More questions than answers for public safety threat risk assessments. Secur J 29, 185–197 (2016). https://doi.org/10.1057/sj.2013.6
Published:
Issue Date:
DOI: https://doi.org/10.1057/sj.2013.6